Quick notes on some tweaks I had to do to get 3CX’s Firewall Check to pass behind my home pfSense firewall:
- Allow PBX to access Google DNS (8.8.8.8): It seems like 3CX is hardcoded to use 8.8.8.8 at the license validation stage. I had blocked 8.8.8.8 on my end to prevent Android and Chromecast devices from preferring external DNS over my local DNS server and this caused the error License_Error httpsError in 3CX.
- Create DHCP-Static mapping for 3CX server.
- Configure NAT Port-forwarding rules: I used the list at https://www.3cx.com/ports-used-3cx-phone-system-v14-v15/ for reference. Table reproduced below.
Protocol
Port (Default)
Description
Port Forwarding Required
TCP
5001 or 443
v15: HTTPs port of Web Server. This port can be configured.
Yes – if you intend on using a 3CX client, Bridge Presence, Remote IP Phones from outside your LAN and 3CX WebMeeting functionality.
TCP
5015
V15: This port is used for the online Web-Based installer wizard (NOT 3CX config command line tool) only during the installation process.
Optional – During the installation process when the Web-Based installer is used from external source
UDP & TCP
5060
3CX Phone System (SIP)
Yes – if you intend on using VoIP Providers, WebRTC and Remote Extensions that are NOT using the 3CX Tunnel Protocol
TCP
5061
3CX Phone System (SecureSIP) TLS
Yes – if you intend on using Secure SIP remote extensions
UDP & TCP
5090
3CX Tunnel Protocol Service Listener
Yes -if you intend on using remote extensions using the 3CX Tunnel Protocol (within the 3CX clients for Windows / Android / iOS) or when using the 3CX Session Border Controller
UDP
9000-9500 (default)
3CX Media Server (RTP) – WAN audio/video/t38 streams
Yes – if you intend on using remote extensions or a VoIP Provider
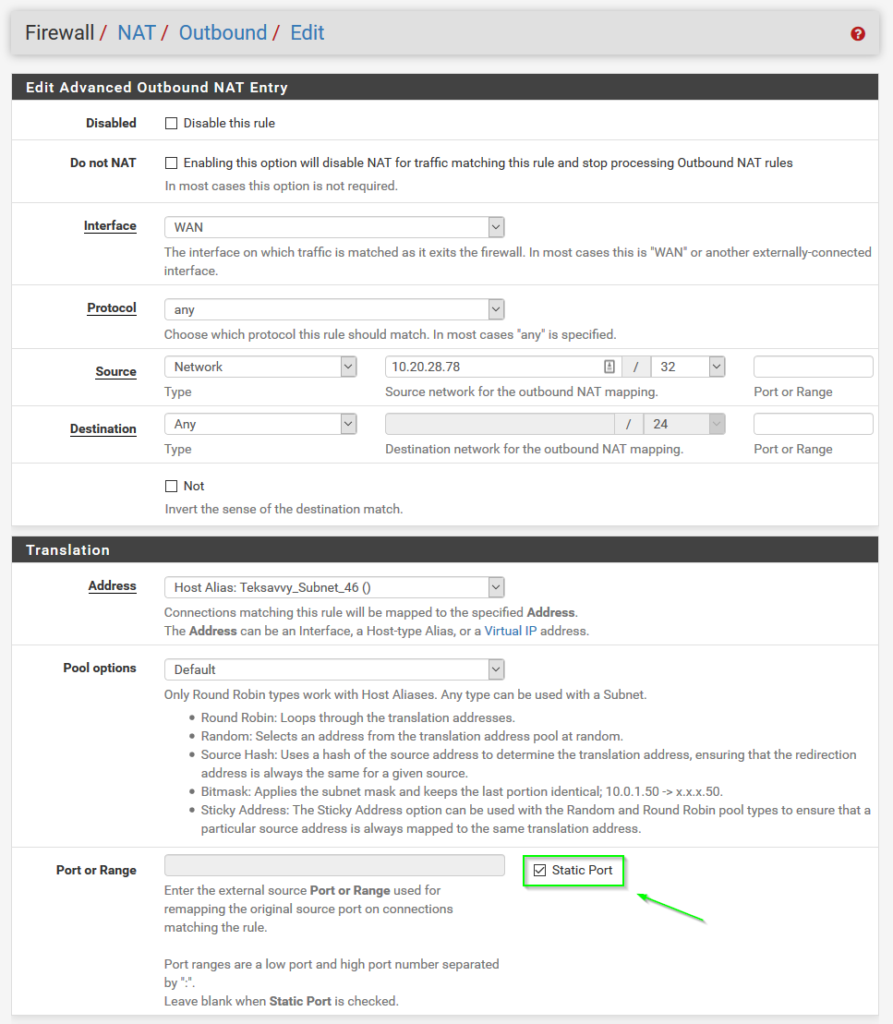
- Configure Outbound NAT Static rule for 3CX server: Automatic Outbound NAT (Default pfSense config) causes a random source port to be used for requests outbound to the Internet. 3CX doesn’t like this behaviour, so we need to add an Advanced Outbound NAT rule to force traffic coming from the 3CX server to use “Static Port” translation, as seen in the following screenshot. For Source, select “Network” and use the 3CX server IP with a mask of /32 (single host).
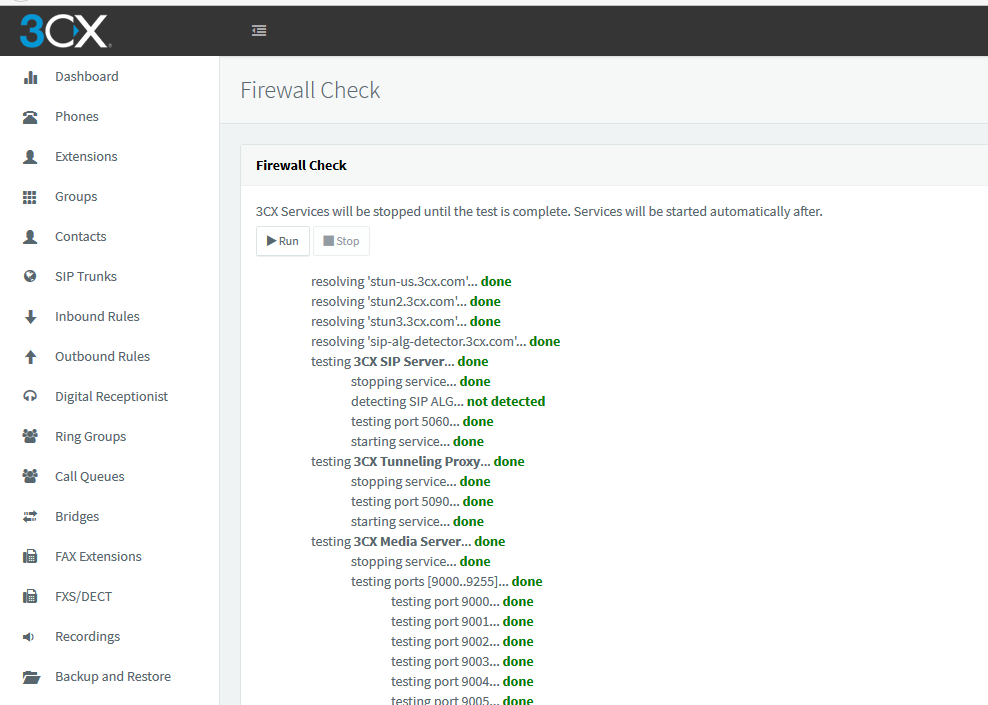
After completing these steps, the 3CX Firewall Check passes all green.