I sometimes have to work from home, which means using VPN. Cisco VPN works quite well, but it’s just not the same as being on the corp network.
Using a spare DD-WRT router (ASUS WL-520GU) running the VPN build of DD-WRT, I set up a persistent VPN connection. Now when I connect my work PC to this router, it behaves just like it’s on the corporate LAN.
How to do it
- First, get the recommended DD-WRT VPN build from dd-wrt.com and flash the router.
- Connect the VPN router’s WAN/Internet port to your home LAN.
- Make sure your router’s LAN IP doesn’t conflict with any subnets in the corp network or your existing home LAN. I used 192.168.133.0/24.
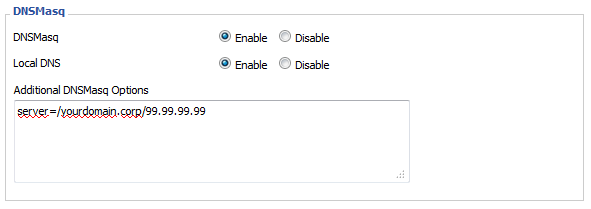
- Add your corporate domains and DNS servers to the dnsmasq config (Services tab)
- Next, customize the script at the end of this post and paste in the Administration>Commands section. Click Save Startup.
- Reboot the router. Wait about 5 minutes (it takes a while to start up) and verify you can ping/access servers on the corp LAN.
- Done!
This isn’t exactly the most stable solution, but it works and I haven’t had any disconnects so far. Also much cheaper and much less trouble than setting up a site-to-site VPN using a real Cisco router.
One sticking point is that from now on any changes to router config (DHCP, WiFi, etc.) will require a reboot. Otherwise your VPN tunnel will die and won’t come back for some reason.
Also, speeds are limited by the router’s processor. Mine is only a 266MHz ARM, so IPsec puts quite a load on it, meaning I can only sustain speeds of about 2Mbps – sadly still better than some of our WAN sites that are using T1 lines.
Script
mkdir /tmp/etc/vpnc
rm -f /tmp/etc/vpnc/vpnc.sh
#Create the VPNC startup script in /tmp
echo '
#!/bin/sh
vpn_concentrator="your.vpn.gateway" ##enter ip or hostname of your Ipsec vpn concentrator
vpn_keepalive_host1="some.server.corp" ##enter the ip or hostname of a computer that is only reachable if vpn connection is established.
vpn_keepalive_host2="other.server.corp" ##enter the ip or hostname of a computer that is only reachable if vpn connection is established.
vpn_groupname="groupname" ##enter the group name here
vpn_grouppasswd="grouppass" ##enter the group password here
vpn_username="user" ##enter your username here
vpn_password="pass" ##enter your password here
#--do not edit this--
#Written by Alain R. 28.Sep.2007
#updated by Matthieu Y. 2012-09-24
vpnc-disconnect
rm -f /tmp/etc/vpnc/vpn.conf
#Create vpnc config file
echo "
IPSec gateway $vpn_concentrator
IPSec ID $vpn_groupname
IPSec secret $vpn_grouppasswd
Xauth username $vpn_username
Xauth password $vpn_password
" >> /tmp/etc/vpnc/vpn.conf
# allow dnsmasq to forward dns replies for LAN subnets
sed -i "s/stop-dns-rebind//g" /tmp/dnsmasq.conf
killall dnsmasq
dnsmasq --conf-file=/tmp/dnsmasq.conf
#Check if we can ping the IPs specified above
pingtest1 () {
ping -q -c1 $param1 >> /dev/null
if [ "$?" == "0" ]; then
echo 0 #reachable
else
echo 1 #not reachable
fi
}
pingtest2 () {
ping -q -c2 $param2 >> /dev/null
if [ "$?" == "0" ]; then
echo 0 #reachable
else
echo 1 #not reachable
fi
}
doloop=true
while [ $doloop==true ]; do
param1=$vpn_keepalive_host1;
if [ "`pingtest1`" == "0" ]; then
sleep 300
else
param2=$vpn_keepalive_host2;
if [ "`pingtest2`" == "0" ]; then
sleep 300
else
doloop=false
vpnc-disconnect
vpnc /tmp/etc/vpnc/vpn.conf --dpd-idle 0
sleep 1
if [ "`pingtest1`" != "0" ]; then
sleep 10
fi
tundev="`ifconfig |grep tun |cut -b 1-4`"
iptables -A FORWARD -o $tundev -j ACCEPT
iptables -A FORWARD -i $tundev -j ACCEPT
iptables -t nat -A POSTROUTING -o $tundev -j MASQUERADE
sleep 9
fi
fi
done
return 0;
' >> /tmp/etc/vpnc/vpnc.sh
chmod 700 /tmp/etc/vpnc/vpnc.sh
/tmp/etc/vpnc/vpnc.sh&
References: